Information
I often come across situations where some unlucky IT Admin is tasked with finding out what happened to X file(s) on a Windows file server or system. When they start their investigation, they come to find out that they are unable to find out who did what to a file or folder, and when it happened.
This is because file system level object access auditing and policies were not enabled prior to the incident. In order to find out what happened, auditing needs to be enabled on the system, and, auditing needs to be configured in the ACL settings of the file or folder.
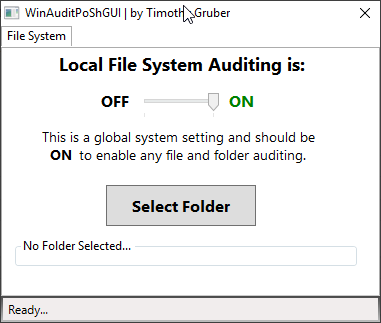
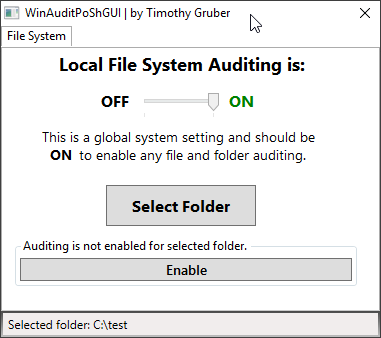
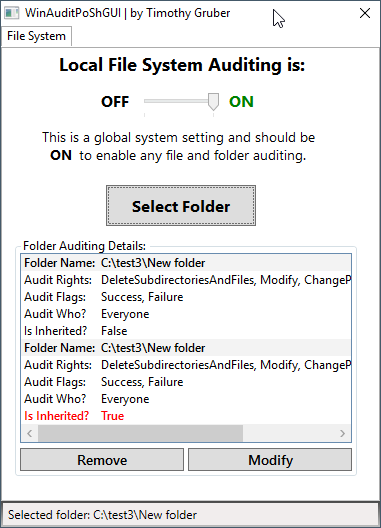
I have created a handy little tool to aide in quickly viewing Windows file system object access auditing policies and settings. It also allows you to turn on auditing, as well as enabling auditing for a chosen folder.
Once Auditing is enabled, the details are found in the Security Event Log.
Screenshots
GitHub Code / Download
The code is available on GitHub, which you can simply run via your favorite method. I have also provided an executable file to make it easier. I used PS2EXE to create the EXE from the provided PowerShell script.
GitHub link: https://github.com/tjgruber/WinAuditPoshGUI
Direct download of .exe: https://github.com/tjgruber/WinAuditPoshGUI/raw/master/WinAuditPoShGUI.exe
Script: https://github.com/tjgruber/WinAuditPoshGUI/blob/master/WinAuditPoShGUI.ps1
If you experience issues or bugs, please submit a GitHub issue. If you have questions, comments, or concerns, please use GitHub issues or the comments below if it’s not directly related to the code.
Future Plans
I plan on adding another tab within the tool for a few quick Security Log configuration settings. When enabling file system auditing, there’s the potential for your security logs to rapidly grow and overwrite security event history, depending on what you are auditing and the policies you use. I hope to address this by making it simple to configure in the next major revision.